Denial of Service (DoS) attacks continue
- kyle Hailey
- Aug 23, 2016
- 3 min read
It’s frustrating to have to spend time jumping off into web security and wordpress configurations when there are so many other things that are important to be doing. Today the DoS continued and the Jetpack solution didn’t seem to work. The other two solutions from Digital Ocean didn’t seem reasonable. One was to re-install wordpress with there install version. Nice that they offer a better security protected version but I didn’t feel like re-installing my wordpress. TH other option basically eliminated all access to xmlrpc.php. Looking around I found a plugin that does firewall work and had just added functionality for the xmlrpc.php problem, called ninjafirewall.
Problem is after I installed it I was getting 500 ” Internal server error” errors trying to access this blog.
Turns out the solution is to add a few lines to /etc/apache2/apache2.conf
such as
<Directory /var/www.kyle>
Options FollowSymLinks
AllowOverride All
</Directory>
where my WordPress files are hosted in /var/www.kyle
This didn’t work and I went down many ratholes trying other things. Problem was there was a another line in my apache2.conf that said
<Directory /var/www>
Options FollowSymLinks
AllowOverride FileInfo
</Directory>
I had done some hacking stuff like changed all “AllowOverride None” to “AllowOverride All” but I hadn’t looked for “AllowOverride FileInfo” and second part is that “/var/www” is a link to “/var/www.kyle” thus overriding my “AllowOverride All” . Long story short changing
<Directory /var/www>
Options FollowSymLinks
AllowOverride FileInfo
</Directory>
to
<Directory /var/www>
Options FollowSymLinks
AllowOverride All
</Directory>
fixed the problem.
Then I was able to install NinjaFirewall and configure it.
Going to the side bar in WordPress admin view, select “Firewall Policies”

then select “Block any access to the API” for “WordPress XML-RPC API”
that works. Now the apache log shows 403 errors for access to xmlrpc.php
root@datavirtualizer:/etc/apache2# tail -f /var/log/apache2/other_vhosts_access.log104.131.152.183:80 154.16.199.74 - - [23/Aug/2016:20:31:47 -0400] "POST /xmlrpc.php HTTP/1.1" 403 376 "-" "Googlebot/2.1 (+http://www.google.com/bot.html)"104.131.152.183:80 154.16.199.74 - - [23/Aug/2016:20:31:47 -0400] "POST /xmlrpc.php HTTP/1.1" 403 376 "-" "Googlebot/2.1 (+http://www.google.com/bot.html)"104.131.152.183:80 154.16.199.74 - - [23/Aug/2016:20:31:48 -0400] "POST /xmlrpc.php HTTP/1.1" 403 376 "-" "Googlebot/2.1 (+http://www.google.com/bot.html)"104.131.152.183:80 154.16.199.74 - - [23/Aug/2016:20:31:48 -0400] "POST /xmlrpc.php HTTP/1.1" 403 376 "-" "Googlebot/2.1 (+http://www.google.com/bot.html)"Actually I think an alternative and better method (don’t trust me I don’t fully understand the options) is to leave the xmlrpc stuff off and got to “login protect” . Choose “only under attack”

see
for more info.
Whoever
154.16.199.74
seems to be the main culprit.
Is there any way to report stuff like this?
IP address 154.16.199.74
Address typeIPv4ISPHost1plus-cloud-serversTimezoneAmerica/Los_Angeles (UTC-7)Local time17:33:55CountryUnited States
State / RegionNevadaDistrict / CountyClark CountyCityLas VegasZip / Postal code89136Coordinates36.1146, -115.173
Update
Decided to see what effect the firewall had in the logs.
The logs look like
04.131.152.183:80 ::1 - - [22/Aug/2016:06:42:05 -0400] "OPTIONS * HTTP/1.0" 200 110 "-"
104.131.152.183:80 ::1 - - [22/Aug/2016:06:42:05 -0400] "OPTIONS * HTTP/1.0" 200 110 "-"
104.131.152.183:80 ::1 - - [22/Aug/2016:06:42:06 -0400] "OPTIONS * HTTP/1.0" 200 110 "-"
104.131.152.183:80 ::1 - - [22/Aug/2016:06:42:06 -0400] "OPTIONS * HTTP/1.0" 200 110 "-"
so we have the date in field 5 and HTML return code in field 10.
Wrote an awk script to get the date truncated to the hour and count of return code by code type by hour
grep xmlrpc $1 | \
sed -e 's/:/ /g' | \
sed -e 's/\[/ /g' | \
awk 'BEGIN {
codes[200]=0;
codes[401]=0;
codes[403]=0;
codes[404]=0;
codes[405]=0;
codes[500]=0;
}
{
dt=sprintf("%s%s",$6,$7);
dates[dt]=dt
cnt[dt,$14]+=1;
}
END {
printf "%14s , ", "date"
for ( code in codes ) {
printf "%7s , " , code
}
for ( dt in dates ) {
printf "\n%14s ", dt
for ( code in codes ) {
printf ", %7i ", cnt[dt,code]+0 ;
}
}
print " "
}'
root@datavirtualizer:/var/log/apache2# ./log.awk other_vhosts_access.log
date , 401 , 403 , 200 , 404 , 500 , 405 ,
24/Aug/201600 , 1757 , 0 , 217 , 0 , 0 , 0
24/Aug/201601 , 2833 , 0 , 96 , 0 , 0 , 2
24/Aug/201602 , 610 , 0 , 502 , 0 , 0 , 1
24/Aug/201603 , 666 , 0 , 401 , 0 , 0 , 1
24/Aug/201604 , 1555 , 0 , 98 , 0 , 0 , 0
24/Aug/201605 , 2927 , 0 , 104 , 0 , 0 , 0
24/Aug/201606 , 3914 , 0 , 98 , 0 , 0 , 1
then plotted in Excel. In Excel just cut and pasted from Unix, chose import wizard and chose comma delineated:

plotting looks like
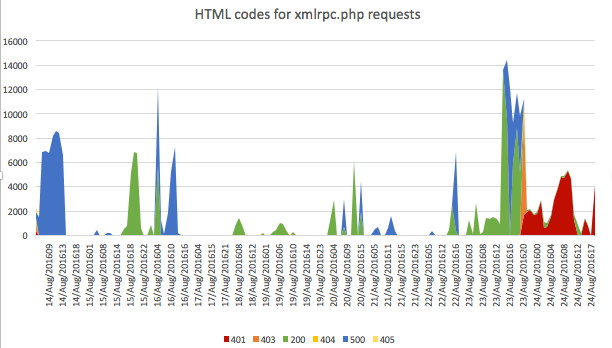
we can see that after applying the firewall at 5pm yesterday , i.e. 17:00 hours, which shows up as 23/Aug/201617 in the x-axis legend, we can see a spike in 403s (forbidden) when I first set up no access to xmlrpc.php and then 401s (unauthorized) after I changed the option to ask for username password after too many access in a few seconds.



Comments